Terminal Commands To Look Like A Hacker
Open Powershell command prompt. If all went well, your Ubuntu terminal shell should look like this. Just your username in the prompt. Now we are ready to add some themes.
- Mac Terminal Commands To Look Like A Hacker
- Terminal Commands To Look Like A Hacker Screen
- Terminal Commands To Look Like A Hacker Minecraft
- How To Look Like A Hacker On Terminal
- How To Look Like A Hacker Using Cmd
To begin, start typing on your keyboard and your hacker code will immediately appear! You can also enter full screen in your browser. To enhance your experience, press Shift or Alt (or Option for Mac) three times. Press Esc to close any dialogs. Configs can be modified in the Settings menu. Look Like a Hacker! (Batch File): In this quick and easy Instructable you can trick your friends into thinking that you hack! Feb 08, 2018 For a more old-school look, consider using Cool Retro Term, which is indeed what it sounds like: A cool retro terminal. I'll use Cool Retro Term for the screenshots below because it does indeed look 100% cooler. The first tool we'll look at is Genact. Feb 13, 2020 Apple users can open the command line of the Terminal, the Mac version of Command Prompt, by using Spotlight search or a general computer search for 'terminal'. 3 Use the Command Prompt or Terminal to imitate hacking. There are many commands that can be used in Windows Command Prompt and Apple Terminal to execute commands or query for information.
Note: commands “w” and “who” may not show users logged from pseudo terminals like Xfce terminal or MATE terminal. The first column shows the username, in this case linuxhint and linuxlat are logged, the second column TTY shows the terminal, the column FROM shows the user address, in this case there are not remote users but if they were you could see IP addresses there. The first tool we'll look at is Genact. Feb 13, 2020 Apple users can open the command line of the Terminal, the Mac version of Command Prompt, by using Spotlight search or a general computer search for 'terminal'. 3 Use the Command Prompt or Terminal to imitate hacking. Like what you see? It even plays Mission Impossible theme music in the background. Moreover, you get a new, random generated hacking terminal each time you run this tool. Let’s see how to become a Hollywood hacker in 30 seconds. How to install Hollywood hacking terminal in Linux. The tool is quite aptly called Hollywood. Jul 20, 2021 Some MacOS users might be intimidated by the Terminal and its commands. When using Terminal on Mac, it might look like you are trying to hack into a system. While of course, it is not the case, knowing Mac Terminal commands will give you an upper hand in mastering the MacOS environment.
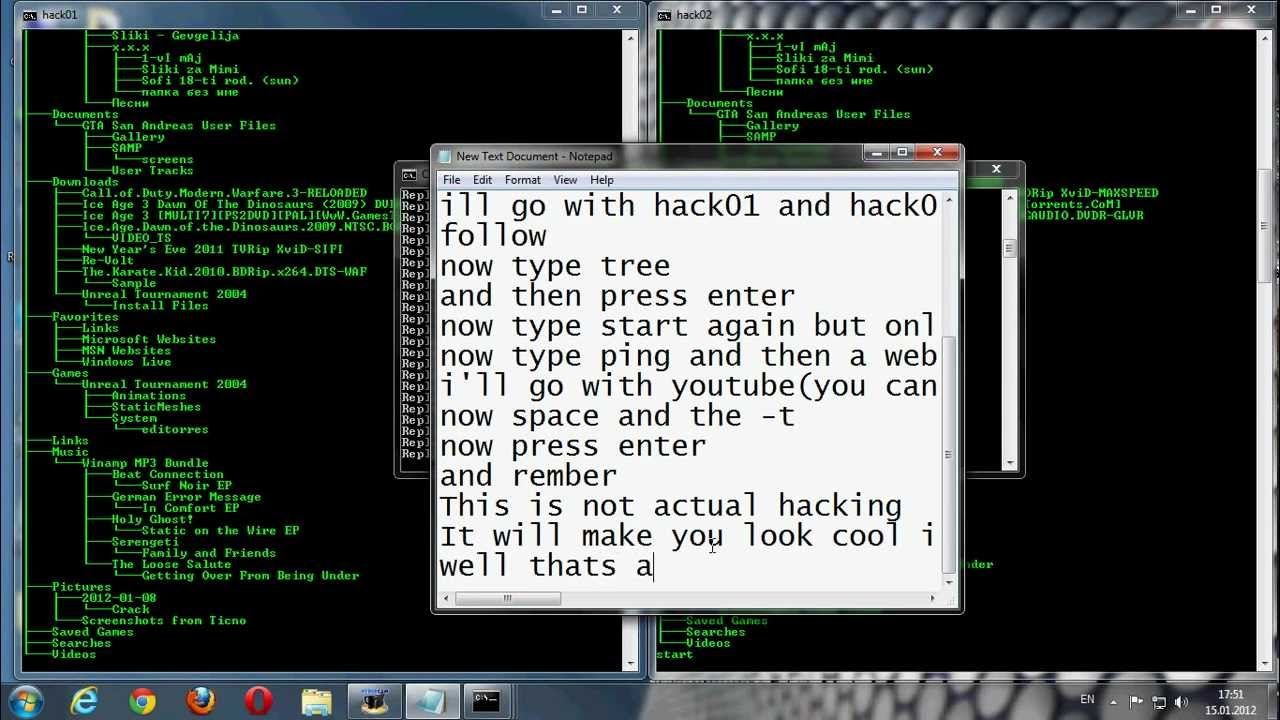
Have you ever wanted to become a hacker just to impress your friends or prank them maybe? Well, I can help you with the top 10 ways to look like a professional hacker. This post won’t teach you any of the hacking techniques, but I assure you’ll get some of the best hacks to fool just about anyone with your “great hacking skills.”
Want to look like a professional hacker minus the learning part?
Then, this post is for you. Now, let’s start with the simple hacks to prank your friends successfully and show off your hacking skills easily.
1. Type Secret Hacking Codes like Hackers
No, I am not asking you to learn to code. It is a simple and one of the best tricks to prank your friends and fool them into thinking you have hacked someone’s computer. Just log in to www.hackertyper.com and press a few keys. Then press Alt key twice.
A pop-up message stating “Access Granted” will be displayed on the screen. You only have to press a few keys to make sure friends believe in your “hacking capabilities.”
2. Change the Command Prompt Color for the Whole Hacker Feel
Have you ever seen the hackers in movies? The ones wearing ski masks typing gibberish codes in green color? Yes, that’s precisely how your friends have seen it too.
Just changing the command prompt text color can help you here. Additionally, you can also change the background color and text transparency from command prompt settings.
For changing the color, run the command prompt and type
color //?
Hit enter and select the number of Green color. Alternately, you can also try other colors of your choice to pass off as a valid hacker in your group.
3. Trick Them with Chrome Passwords
People are lazy, and that includes your friends. I am sure at least 90% of your friends have saved their passwords on chrome for quicker log in time. Now, you can use this to your advantage.
Just type chrome://settings/passwords in the URL tab and hit enter. From here, you can steal all your friends’ saved passwords and log into their social media. This way will surely make them believe your story.
4. Inspect Element to Reveal Passwords
Shock your friend by stealing their Facebook passwords. It’s quite simple.
As you know, passwords are hidden by default. If your friends have entered a password, just click on the password tab and right click to Inspect Element. Now, change the text type from password to text. This action will reveal the hidden password, and you can make your friends think you did it with rigorous hacking.
This method is one of the best ways to look like a professional hacker using modern browsers including Chrome, Safari, Firefox.
5. Shutdown your Friend’s PC with your Custom Message
Here’s a brief code you can write on the notepad to shut down your friend’s PC without them knowing. Using this method, you can easily trick them into believing you have hacked their system.
Open the notepad and type the fun code:
@echo off
Shutdown.exe -s -t 10
Cls
msg* I told you not to mess with me!
Now, save this file as myvirus.bat
Your first virus made in notepad is ready!
6. Deploy Keylogger Software on your Friend’s Phone or PC
It is a reasonably simple way to look like a professional hacker in front of your friends. Take any of your friend’s phone or PC and download a keylogger software on it. A keylogger software essentially keeps a record of every keystroke and stores it in a log file.
Using this method, you can gain access to your friends’ passwords and show it to them later on.
7. Fake Windows Data Transfer Progress Bar to Prank your Buddies
Download this fake progress bar, and you’re good to go. You can also customize the icons, buttons, speed and progress bar message. Just tell your friends you have hacked into someone’s PC and show them the progress bar.
Your superior hacking skills will spellbind them.
8. Makeover your PC for the Look and Feel of a Hacker’s PC
Download Rainmeter and change the whole look of your PC. Rainmeter is one of the best Utility software for Windows PC that’ll give you the entire look and feel of a hacker’s PC using a Rainmeter hacker theme. Just bring your friends’ home and look at their surprised reactions at your hacking gadget.
Rainmeter is available for download free of cost.
9. Give your Laptop the Personality that Shouts Hacker
“What they will see, they will believe.” In simple words, you have to change the look of your laptop that screams hacker whenever your friends see it. Show your passion for hacking everywhere.
Purchase a laptop skin which is “hacker inspired” and select wallpapers that are mysterious and geeky to make your prank successful.
10. Prank your Friends with Resource Hacker
Resource Hacker is a free tool that you can use to prank your friends. Download this free software and modify the values to tell your friends how you’ve decompiled this software and then recompiled it with your modifications.
They’ll be stunned.
Wrapping Up
That’s all for this post!
These were my top 10 hacks or ways to look like a professional hacker in front of your friends. Try some or all of these methods to play a prank on your gullible friends, and they’ll believe you’re a hacker in no time.
Let me know if it worked for you or share some of your tricks. I’d love to hear from you.
Until next time. Happy Pranking!
Just about every geek and nerd that wants to be a hacker always wants to skip straight to the good stuff, and it’s no wonder why. There’s a certain amount of mystery, intrigue, and awe in being able to used advanced tools (such as those found on Kali Linux like Metasploit) to hack into another computing system. Hackers have been around for decades now, and are frequently present in action and thriller films, such as The Matrix. And to be fair, we’ve gone through some detailed guides that show how to use these tools.
For instance, we’ve already covered NMAP, Metasploit, and other similar tools. But there’s one big problem. These tools work almost exclusively at the command line, or in Linux, the BASH shell. And even the highest quality guides are flawed – especially in the hands of a newb. You see, a single article can’t hope to cover every eventuality, caveat, an ‘gotchas.’
Computers are composed of individual parts made all around the world, and assimilated as a hodgepodge of different manufacturers’ parts. The amount and type of memory, wireless card, processor architecture, HDD or SDD, peripheral devices, and more vary greatly from system to system, and Kali (or for that matter, Linux) can’t hope to to run exactly the same on every different piece of hardware.
Even if you’re hacking guide is highly detailed, chances are that you’ll run into a surprising error that doesn’t fit in nicely with your guide’s 12 easy steps. And most guides can’t hope to account for every single error. Doing so would lie far outside the scope of the guide.
As such, it’s imperative that hackers and penetration testers who want to learn how to hack have a solid foundational knowledge of common BASH shell concepts. Look folks, though they may not be the most ‘sexy’ commands, there are some simple commands that you need to know like the back of your hand.
If you get caught on the job not knowing how to run these simple commands, you’re likely going to get laughed out of the office – and perhaps even be handed a pink slip. So, today we’re going to be talking about general purpose BASH commands that you really need to know before moving on to advanced hacking topics. Basically, you need to be comfortable in a command line environment, so let’s start with one of my favorites: network interface configuration commands.
The network interface commands are also exceptionally useful for troubleshooting connectivity problems. Also, note that with few exceptions, the following commands are mostly universal. That is, they can be utilized on almost all varieties of Linux, and some of them can even be used in an OSX environment since Mac OSX is a descendant of BSD.
For reference, we are going to be taking a closer look at how to make shell configurations regarding the following topics:
Network interfaces
Canceling commands
Default gateways and routes
Piping commands
Viewing and killing processes
File system navigation
Many of these topics will be useful to those wishing to test for Linux certifications such as the Comptia Linux+ or LPI certs. To put it bluntly, you should really know these basics before trying to run advanced packet capture and Metasploit demos. So, without further adieu, let’s start with the network interface commands.
Network Interfaces
Whether using an internal wireless card in your laptop, Ethernet, or an external USB wireless interface, you had better darn well know how to configure them. Just about all of the wireless hacking demos we’ve run involve configuring a wireless interface in some way, and you need to know how read their current configuration. So, let’s start with the basics. The following command pulls up current interface configuration data:
ifconfig
Those of you who have worked in the Windows command prompt can easily remember this command, because it only has a single character that varies from the Window’s ipconfig command. Go ahead and run it, and notice that all of the data is separated by interface.
This command is incredibly useful because it will quickly display encapsulation type, MAC address, IP address, broadcast address, subnet mask, transmit and receive packet-count, total information sent over the interface, and other useful information. But it doesn’t show all the available data for that interface. For a more detailed report of interface data, simply run the following command:
ifconfig -a
In the command listed above, the -a parameter indicates ‘all.’ It will show incredibly detailed information that is useful to network engineers, and can help troubleshoot network interface problems. If your terminal window is getting too messy, you can simply enter the clear command to clear things up a bit. Also, you can run ifconfig followed by an interface’s name to only display parameters for that individual interface.
Furthermore, you’re going to need to know how to bring an interface online and offline (or up and down). Often times, after making a configuration change to an individual interface, it’s necessary to ‘bounce’ the interface by bringing it down, and then bringing it up again. You do need to have administrative privilges to run these commands. Also, note that if you’re running a live version of Linux – such as one installed on a bootable USB flash drive like Ubuntu Live – you’ll likely need to precede the commands with the sudo command.
ifconfig [interface_name] down
ifconfig [interface_name] up
So, for instance, if I wanted to reset my Ethernet interface, I would run the ifconfig eth0 down command. After waiting for a decent amount of time (30 seconds at least to be safe), I’d then run the ifconfig eth0 up. Note that the interface’s name includes a zero rather than the letter of the alphabet sandwiched between ‘N’ and ‘P.’ Your interface names may differ, too, so just run the ifconfig command to display the interfaces’ names.
And arguably, one of the largest reasons that Linux is so powerful is due to it’s command line. You can make configurations within seconds without having to go through long and contrived GUI windows to find the correct setting. It would be a good idea to know how to change IP address information on a per-interface basis as follows:
ifconfig eth0 10.1.1.2
ifconfig eth0 netmask 255.255.255.0
ifconfig eth0 broadcast 10.1.1.255
In order, these commands will set the IP address, subnet mask, and broadcast address of the specified interface – which is eth0 in this example. Next up, you’ll also want to know how to set an interface in promiscuous mode. This is an undoubtedly crucial tool for most kinds of wireless hacking, so let’s first define what this mode does.
Through various network mediums and address types (such as broadcast frames on wireless interfaces or broadcast data like ARP protocol data), an interface can be presented with frames that weren’t addressed to the receiving interface. The default action of the interface is to drop these packets, since it’s not the intended destination. However, many attacks leverage the information contained within the frames and packets.
By setting the interface in promiscuous mode, the interface will receive and process the frames that weren’t intended for it, and instead send them to the CPU for processing. Use the following command:
ifconfig eth0 promisc
This mode of operation is frequently used in a lot of different network tools, such as protocol analyzers and packet captures. If you want to shut off promiscuous mode on an interface, simply run the following command:
ifconfig eth0 -promisc
Canceling a Command
Sometimes, for whatever reason, you may find that a command has frozen, locked up, or is simply taking too long to complete. Linux novices typically find this incredibly frustrating, and don’t know how to cancel the command. Instead, they simply close out the terminal window and open a new one – but there’s a much simpler way. Simply issue the following command hotkey to cancel currently running command or one that is hanging:
ctrl + c
Mac Terminal Commands To Look Like A Hacker
To test it out, run something like a ping command. For instance, ping Google’s DNS servers with the ping 8.8.8.8 command. You’ll notice that the shell will continue pinging the server on an endless loop. To stop the ping operation, just run the ctrl + c command and it should terminate.
Terminal Commands Mac For Look Like A Hacker Website Prank
Default Gateway and Routes
Every competent network engineer and penetration tester should have a firm grasp on routing technologies. It’s fairly atypical to setup custom routes for an individual computer, because that function is typically controlled by routers. Nevertheless, you should know how to view your Linux system’s routing table. And the command couldn’t be simpler, as follows:
route
The most practical purpose for this command is to check and verify your default route. In a home setting, the default route is going to almost always be your wireless router. But in corporate and professional network environments, there may be more complex configurations.
Piping Commands
One of the wonderful and powerful qualities of the BASH shell is that one command’s output can be used as input for another command. These features are unbelievably flexible, and allow for command formatting and complex configurations. However, we’re only going to be discussing the most rudimentary of piping techniques today.
You may have noticed that sometimes when entering a command, the entire shell window fills up with loads of text that all flit by in fractions of a second. If you want to read the output page by page, you can simply pipe it to the less command. The pipe symbol is located directly above the enter key on most keyboards, and looks like a solid vertical line. The syntax to pipe command output to less follows:
[command] | less
We’re going to be using this in the services and daemons section, but for now test it out on a simple command. For instance, issue the following command:
ifconfig -a | less
Doing so will display your network interface information one page at a time. Now you can use the arrow keys to move up and down the output, or hit the spacebar to move down an entire page. If you want to exit the output display, simply type the ‘q’ key to quit and be returned to the command prompt.
Viewing and Killing Currently Running Processes
There are a seemingly endless number of process running diligently in the background of your Linux system. It would be of great benefit to know how to view them and potentially kill them. Sometimes a process might malfunction, and even cause a memory leak. There are so many processes that, for the sake of this demonstration, we’re going to be piping the command output to less. Run the following command:
ps aux | less
Note that there are actually several ways to view currently running processes, too. Alternatively, you can use the jobs or top commands. They will show you related information, such as the owner, process ID, and other vital information about background processes.
However, once in a while, you may need to shut one of these processes down. It’s rare for a process to render a Linux system completely unusable. Nevertheless, runaway and zombie background processes aren’t uncommon in a Window’s environment. And you should also consider that Linux is susceptible to viruses more than ever before. So, being able to kill a process is crucial. Simply use the following command:
kill[process_id]
For example, if I wanted to kill my Firefox process because it crashed and wasn’t behaving properly, I would issue the command as follows:
kill 17648
It’s just a matter of looking up the process ID before running the kill command.
File System Navigation
Though understanding the entirety of the Linux file system lies far outside the scope of this guide, knowing how to navigate the file system from the command line is one of the most basic and fundamental skills. The first command you need to know relates to knowing which directory you reside in.
In Linux, this is known as your current working directory. And the command to display that information is known as the print working directory command, as follows:
pwd
By default, you’re likely in the home directory. To change directories, simply use the following command:
cd [directory]
For instance, if I wanted to change to the root directory (assuming I had root privileges), I would type ‘cd /’. Also, if you simply wanted to move up one level to the next highest directory, you can issue the ‘cd ./’ command. But knowing what files and folders are available for navigation requires you to run the list command. Doing so will show you all files and folders within your current working directory. The basic command is as follows:
Terminal Commands Mac For Look Like A Hacker On Roblox
ls
This command will simply display common files and folders, but it has several useful parameters to display more information. If you wished to view the read, write, and edit permissions for the current user or group, simply issue a long-listing command as follows:
ls -l
This command will also display when a file was created or last edited, though it won’t display hidden files. If you’re trying to make a configuration change to an application file, it will likely be hidden, so simply run the following command:
ls -a
Terminal Commands Mac For Look Like A Hacker In Cmd
Note that all of the hidden files and folders will be preceded with the ‘.’ character. There are actually a lot of different flags that can be used with the ls command, but this should suffice for basic file system navigation. Between the ls, cd, and pwd commands, you should be able to navigate throughout your HDD/SDD’s Linux file system by only using the terminal.
Final Thoughts
These don’t make up every foundational command that you should learn in order to be competent using the BASH shell. However, these are certainly some of the most important from a perspective of penetration testing and hacking. In particular, you should learn the ifconfig and route commands, and know them like the back of your hand.
If you’re new to the BASH shell, I’d learn these commands – and learn them well – before pursuing harder tutorials. But after using the shell for a while, perhaps as little as a week or two, they should become second nature to you. And having the ability to pull up all of this information on the fly is what makes Linux so powerful.
You won’t have to navigate through a tedious organization of text fields and GUI windows. Though Windows does have the CMD prompt, it isn’t anywhere near as powerful as the BASH shell. Once you factor in the ability to write and run scripts and use advanced tools like Metasploit, you’ll begin to understand what makes Kali Linux so formidable. Stay tuned for more tutorials as well, because we’ll run through tutorials to help demystify the most popular Kali command line tools that hackers and penetration testers use to break other computing systems.
Over the course of our many lessons and adventures, we have learned a lot about the shell, and explored many of the common command line utilities found on Linux systems. There is, however, one program we have overlooked, and it may be among the most important and most frequently used of them all-- our terminal emulator.
In this adventure, we are going to dig into these essential tools and look at a few of the different terminal programs and the many interesting things we can do with them.
A Typical Modern Terminal
Graphical desktop environments like GNOME, KDE, LXDE, Unity, etc. all include terminal emulators as standard equipment. We can think of this as a safety feature because, if the desktop environment suffers from some lack of functionality (and they all do), we can still access the shell and actually get stuff done.
Modern terminal emulators are quite flexible and can be configured in many ways:
gnome-terminal preferences dialog
Size
Terminal emulators display a window that can be adjusted to any size from the sublime to the ridiculous. Many terminals allow configuration of a default size.
The 'normal' size for a terminal is 80 columns by 24 rows. These dimensions were inherited from the size of common hardware terminals, which, in turn, were influenced by the format of IBM punch cards (80 columns by 12 rows). Some applications expect 80 by 24 to be the minimum size, and will not display properly when the size is smaller. Making the terminal larger, on the other hand, is preferable in most situations, particularly when it comes to terminal height. 80 columns is a good width for reading text, but having additional height provides us with more context when working at the command line.
Another common width is 132 columns, derived from the width of wide fan-fold computer paper. Though this is too wide for comfortable reading of straight text (for example, a man page), it's fine for other purposes, such as viewing log files.
The 80-column default width has implications for the shell scripts and other text-based programs we write. We should format our printed output to fit within the limits of an 80-character line for best effect.
Tabs
A single terminal window with the ability to contain several different shell sessions is a valuable feature found in most modern terminal emulators. This is accomplished through the use of tabs.
Tabs are a fairly recent addition to terminal emulators, first appearing around 2003 in both GNOME's gnome-terminal and KDE's konsole.
Profiles
Another feature found in several modern terminals is multiple configuration profiles. With this feature, we can have separate configurations for different tasks. For example, if we are responsible for maintaining a remote server, we might have a separate profile for the terminal that we use to manage it.
Fonts, Colors, Backgrounds
Most terminal emulators allow us to select fonts, colors, and backgrounds for our terminal sessions. The three most important criteria for selecting fonts, colors, and backgrounds are: 1. legibility, 2. legibility, and 3. legibility. Many people post screen shots of their Linux desktops online, and there is a great fascination with 'stylish' fonts, faint colors, and pseudo-transparent terminal windows, but we use our terminals for very serious things, so we should treat our terminals very seriously, too. No one wants to make a mistake while administering a system because they mis-read something on the screen. Choose wisely.
Past Favorites
When the first graphical environments began appearing for Unix in the mid-1980s, terminal emulators were among the first applications that were developed. After all, the GUIs of the time had very little functionality and people still needed to do their work. Besides, the graphical desktop allowed users to display multiple terminal windows- a powerful advantage at the time.
xterm
The granddaddy of all graphical terminals is xterm, the standard terminal emulator for the X Window System. Originally released in 1984, it's still under active maintenance. Since it is a standard part of X, it is included in many Linux distributions. xterm was very influential, and most modern terminal programs emulate its behavior in one way or another.
xterm with default configuration
In its default configuration, xterm looks rather small and pathetic, but almost everything about xterm is configurable. When we say 'configurable,' we don't mean there is a pretty 'Preferences' dialog. This is Unix! Like many early X applications, it relies on an Xresources file for its configuration. This file can be either global (/etc/X11/Xresources) or local to the user (~/.Xresources). Each item in this file consists of an application class and a setting. If we create the file ~/.Xresources with the following content:
then we get a terminal like this:
A complete list of the Xresources configuration values for xterm appears in its man page.
While xterm does not appear to have menus, it actually has 3 different ones, which are made visible by holding the Ctrl key and pressing a mouse button. Different menus appear according to which button is pressed. The scroll bar on the side of the terminal has a behavior like ancient X applications. Hint: after enabling the scroll bar with the menu, use the middle mouse button to drag the slider.
Though xterm offers neither tabs nor profiles, it does have one strange extra feature: it can display a Tektronix 4014 graphics terminal emulator window. The Tektronix 4014 was an early and very expensive storage tube graphics display that was popular with computer aided design systems in the 1970s. It's extremely obscure today. The normal xterm text window is called the VT window. The name comes from the DEC VT220, a popular computer terminal of the same period. xterm, and most terminals today, emulate this terminal to a certain extent. xterm is not quite the same as the VT terminal, and it has its own specific terminfo entry (see the tput adventure for some background on terminfo). Terminals set an environment variable named TERM that is used by X and terminfo to identify the terminal type, and thus send it the correct control codes. To see the current value of the TERM variable, we can do this:
Even if we are using a modern terminal, such as gnome-terminal, we will notice that the TERM variable is often set to 'xterm' or 'xterm-color'. That's how much influence xterm had. We still use it as the standard.
rxvt
By the standards of the time, xterm was a heavyweight program but, as time went by, some of its features were rarely used such as the Tektronix emulation. Around 1990, in an attempt to create a simpler, lighter terminal emulator, Robert Nation wrote rxvt as part of the FVWM window manager, an early desktop environment for Unix-like systems.
rxvt has a smaller feature set than xterm and emulates the DEC VT 102 terminal rather than the more advanced VT 220. The last remnant pc save game editor. rxvt sets the TERM variable to 'rxvt', which is widely supported. Like xterm, rxvt has menus that are displayed by holding the Ctrl key and pressing different mouse buttons.
rxvt is still under active maintenance, and there is a popular modern implementation forked from the original called urxvt (rxvt-Unicode) by Mark Lehmann, which supports Unicode (multi-byte characters used to express a wider range of written languages than ASCII). One interesting feature in urxvt is a daemon mode that allows launching multiple terminal windows all sharing the same instance of the program- a potential memory saver.
urxvt with default configuration
Like xterm, rxvt uses Xresources to control its configuration. The default rxvt configuration is very spare. Adding the following settings to our Xresources file will make it more palatable (urxvt shown):
Modern Power Terminals
Most modern graphical desktop environments include a terminal emulator program. Some are more feature-rich than others. Let's look at some of the most powerful and popular ones.
gnome-terminal
The default terminal application for GNOME and its derivatives such as Ubuntu's Unity is gnome-terminal. Possibly the world's most popular terminal app, it's a good, full-featured program. It has many features we expect in modern terminals, like multiple tabs and profile support. It also allows many kinds of customization.
Tabs
Busy terminal users will often find themselves working in multiple terminal sessions at once. It may be to perform operations on several machines at the same time, or to manage a complex set of tasks on a single system. This problem can be addressed either by opening multiple terminal windows, or by having multiple tabs in a single window.
The File menu in gnome-terminal offers both choices (well, in older versions anyway). In newer versions, use the keyboard shortcut Ctrl-Shift-T to open a tab. Tabs can be rearranged with the mouse, or can be dragged out of the window to create a new window. With gnome-terminal, we can even drag a tab from one terminal window to another.
Keyboard shortcuts
Since, in an ideal universe, we never lift our fingers from the keyboard, we need ways of controlling our terminal without resorting to a mouse. Fortunately, gnome-terminal offers a large set of keyboard shortcuts for common operations. Here are some of the most useful ones, defined by default:
| Shortcut | Action |
|---|---|
| Ctrl-Shift-N | New Window |
| Ctrl-Shift-W | Close Window |
| F11 | View terminal full screen |
| Shift-PgUp | Scroll up |
| Shift-PgDn | Scroll down |
| Shift-Home | Scroll to the beginning |
| Shift-End | Scroll to the end |
| Ctrl-Shift-T | New Tab |
| Ctrl-Shift-Q | Close Tab |
| Ctrl-PgUp | Next Tab |
| Ctrl-PgDn | Previous Tab |
| Alt-n | Where n is a number in the range of 1 to 9, go to |
| tab n |
Keyboard shortcuts are also user configurable.
While it is well known that Ctrl-c and Ctrl-v cannot be used in the terminal window to perform copy and paste, Ctrl-Shift-C and Ctrl-Shift-V will work in their place with gnome-terminal.
Profiles
Profiles are one of the great, unsung features of many terminal programs. This may be because their advantages are perhaps not intuitively obvious. Profiles are particularly useful when we want to visually distinguish one terminal session from another. This is especially true when managing multiple machines. In this case, having a different background color for the remote system's session may help us avoid typing a command into the wrong session. We can even incorporate a default command (like ssh) into a profile to facilitate the connection to the remote system.
Let's make a profile for a root shell. First, we'll go to the File menu and select 'New Profile..' and when the dialog appears enter the name 'root' as our new profile:
Next, we'll configure our new profile and choose the font and default size of the terminal window. Then we will choose a command for the terminal window when it is opened. To create a root shell, we can use the command sudo -i. We will also make sure to specify that the terminal should exit when the command exits.
Setting the command in the configuration dialog
Finally, we'll select some colors. How about white text on a dark red background? That should convey an appropriate sense of gravity when we use a root shell.
Once we finish our configuration, we can test our shell:
Root profile gnome-terminal
We can configure terminal profiles for any command line program we want: Midnight Commander, tmux, whatever.
Here is another example. We will create a simple man page viewer. With this terminal profile, we can have a dedicated terminal window to only display man pages. To do this, we first need to write a short script to prompt the user for the name of which command to look up, and display the man page in a (nearly) endless loop:
We'll save this file in our ~/bin directory and use it as our custom command for our terminal profile.
Next, we create a new terminal profile and name it 'man page'. Since we are designing a window for man pages, we can play with the window size and color. We'll set the window tall and a little narrow (for easier reading) and set the colors to green text on a black background for that retro terminal feeling:
Man page gnome-terminal window
Opening hyperlinks and email addresses
One of the neat tricks gnome-terminal can do is copy and/or open URLs. When it detects a URL in the stream of displayed text, it displays it with an underline. Right-clicking on the link displays a menu of operations:
Resetting the terminal
Sometimes, despite our best efforts, we do something dumb at the terminal, like attempting to display a non-text file. When this happens, the terminal emulator will dutifully interpret the random bytes as control codes and we'll notice that the terminal screen fills with garbage and nothing works anymore. To escape this situation, we must reset the terminal. gnome-terminal provides a function for this located in its Terminal menu.
konsole
konsole, the default terminal application for the KDE desktop, has a feature set similar to that of gnome-terminal. This, of course, makes sense since konsole directly 'competes' with gnome-terminal. For instance, both gnome-terminal and konsole support tabs and profiles in a similar fashion.
konsole does have a couple of unique features not found in gnome-terminal. konsole has bookmarks, and konsole can split the screen into regions allowing more than one view of the same terminal session to be displayed at the same time.
Bookmarks
konsole allows us to store the location of directories as bookmarks. Locations may also include remote locations accessible via ssh. For example, we can define a bookmark such as ssh:me@remotehost, and it will attempt to connect with the remote system when the bookmark is used.
konsole bookmarks menu
Split View
konsole's unique split view feature allows us to have two views of a single terminal session. This seems odd at first glance, but is useful when examining long streams of output. For example, if we needed to copy text from one portion of a long output stream to the command line at the bottom, this could be handy. Further, we can get views of different terminal sessions, by using using tabs in conjunction with split views, since while the tabs will appear in all of the split views, they can be switched independently in each view:
konsole with tabs and split view
guake
gnome-terminal has spawned a couple of programs that reuse many of its internal parts to create different terminal applications. The first is guake, a terminal that borrows a design feature from a popular first-person shooter game. When running, guake normally hides in the background, but when the F12 key is pressed, the terminal window 'rolls down' from the top of the screen to reveal itself. This can be handy if terminal use is intermittent, or if screen real estate is at a premium.
guake shares many of the configuration options with gnome-terminal, as well as the ability to configure what key activates it, which side of the screen it rolls from, and its size.
Though guake supports tabs, it does not (as of this writing) support profiles. However, we can approximate profiles with a little clever scripting:
After saving this script, we can open new tabs in guake by entering the command gtab followed by an optional profile, either 'root' or 'man' to duplicate what we did with the gnome-terminal profiles above. Entering gtab without an option simply opens a new tab in the current working directory.
As we can see, guake has a number of interesting command line options that allow us to program its behavior.

For KDE users, there is a similar program called yakuake.
terminator
Like guake, terminator builds on the gnome-terminal code to create a very popular alternative terminal. The main feature addition is split window support.
terminator with split screens
By right-clicking in the terminator window, terminator displays its menu where we can see the options for splitting the current terminal either vertically or horizontally.
Once split, each terminal pane can dragged and dropped. Panes can also be resized with either the mouse or a keyboard shortcut. Another nice feature of terminator is the ability to set the focus policy to 'focus follows mouse' so that we can change the active pane by simply hovering the mouse over the desired pane without have to perform an extra click to make the pane active.
The preferences dialog supports many of the same configuration features as that of gnome-terminal, including profiles with custom commands:
The terminator preferences dialog
A good way to use terminator is to expand its window to full screen and then split it into multiple panes:
We can even automate this by going into Preferences/Layouts and storing our full screen layout (let's call it '2x2') then, by invoking terminator this way:
to get our layout instantly.
Terminals for other platforms
Android
While we might not think of an Android phone or tablet as a Linux computer, it actually is, and we can get terminal apps for it which are useful for administering remote systems.
Connectbot
Connectbot is a secure shell client for Android. With it, we can log into any system running an SSH server. To the remote system, Connectbot looks like a terminal using the GNU Screen terminal type.
One problem with using a terminal emulator on Android is the limitations of the native Google keyboard. It does not have all the keys required to make full use of a terminal session. Fortunately, there are alternate keyboards that we can use on Android. A really good one is Hacker's Keyboard by Klaus Weidner. It supports all the normal keys, Ctrl, Alt, F1-F10, arrows, PgUp, PgDn, etc. Very handy when working with vi on a phone.
Connectbot with Hacker's Keyboard on Android
Termux
The Termux app for Android is unexpectedly amazing. It goes beyond being merely an SSH client; it provides a full shell environment on Android without having to root the device.
After installation, there is a minimal base system with a shell (bash) and many of the most common utilities. Initially, these utilities are the ones built into busybox (a compact set of utilities joined into a single program that is often used in embedded systems to save space), but the apt package management program (like on Debian/Ubuntu) is provided to allow installation of a wide variety of Linux programs.
We can have dot files (like .bashrc) and even write shell scripts and compile and debug programs in Termux. Pretty neat.
When executing ssh, Termux looks like an 'xterm-256color' terminal to remote systems.
Chrome/Chrome OS
Google makes a decent SSH client for Chrome and Chrome OS (which is Linux, too, after all) that allows logging on to remote systems. Called Secure Shell, it uses hterm (HTML Terminal, a terminal emulator written in JavaScript) combined with an SSH client. To remote systems, it looks like a 'xterm-256color' terminal. It works pretty well, but lacks some features that advanced SSH users may need.
Secure Shell is available at the Chrome Web Store.
Terminal Commands To Look Like A Hacker Screen
Secure Shell running on Chrome OS
Summing Up
Given that our terminal emulators are among our most vital tools, they should command more of our attention. There are many different terminal programs with potentially interesting and helpful features, many of which, most users rarely, if ever, use. This is a shame since many of these features are truly useful to the busy command line user. We have looked at a few of the ways these features can be applied to our daily routine, but there are certainly many more.
Further Reading
- 'The Grumpy Editor's guide to terminal emulators' by Jonathan Corbet: https://lwn.net/Articles/88161/
xterm:
xterm on Wikipedia: https://en.wikipedia.org/wiki/Xterm
Homepage for the current maintainer of xterm, Thomas Dickey: https://invisible-island.net/xterm/
Tektronix 4014:
Tektronix 4014 on Wikipedia: https://en.wikipedia.org/wiki/Tektronix_4010
Some background on the 4014 at Chilton Computing: http://www.chilton-computing.org.uk/acd/icf/terminals/p005.htm
rxvt:
- Home page for rxvt: http://rxvt.sourceforge.net/
urxvt (rxvt-Unicode):
- Home page for the rxvt-Unicode project: http://software.schmorp.de/pkg/rxvt-unicode.html
gnome-terminal:
- Help pages for gnome-terminal: https://help.gnome.org/users/gnome-terminal/stable/
konsole:
- The Konsole Manual at the KDE Project: https://docs.kde.org/stable5/en/applications/konsole/index.html
guake:
The home page for the guake project: http://guake-project.org/
The Arch Wiki entry for guake (contains a lot of useful information but some is Arch Linux specific): https://wiki.archlinux.org/index.php/Guake
terminator:
- The home page for the terminator project: https://gnometerminator.blogspot.com/p/introduction.html
Connectbot:
- Connectbot at the Google Play Store: https://play.google.com/store/apps/details?id=org.connectbot&hl=en
Hacker's Keyboard:
- Hacker's Keyboard at the Google Play Store: https://play.google.com/store/apps/details?id=org.pocketworkstation.pckeyboard&hl=en
Termux:
Terminal Commands To Look Like A Hacker Minecraft
- Termux at the Google Play Store: https://play.google.com/store/apps/details?id=com.termux&hl=en
How To Look Like A Hacker On Terminal
Secure Shell
Secure Shell at the Chrome Web Store: https://chrome.google.com/webstore/detail/secure-shell-app/pnhechapfaindjhompbnflcldabbghjo
Secure Shell FAQ: https://chromium.googlesource.com/apps/libapps/+/master/nassh/doc/FAQ.md
© 2000-2021,William E. Shotts, Jr.Verbatim copying and distribution of this entire article ispermitted in any medium, provided this copyright notice is preserved.
How To Look Like A Hacker Using Cmd
Linux® is a registered trademark of Linus Torvalds.